Falcon for AWS
Learn more >
CrowdStrike Cloud Security delivers comprehensive breach protection for workloads, containers, and Kubernetes enabling organizations to build, run, and secure cloud-native applications with speed and confidence.
CrowdStrike is recognized by Frost & Sullivan as a leader in the 2022 Frost Radar™️: Cloud-Native Application Protection Platform, 2022 report. CrowdStrike was also named a Winner in the 2022 CRN Tech Innovator Awards for the Best Cloud Security category. Both accolades underscore CrowdStrike's growth and innovation in the CNAPP market. Learn more >

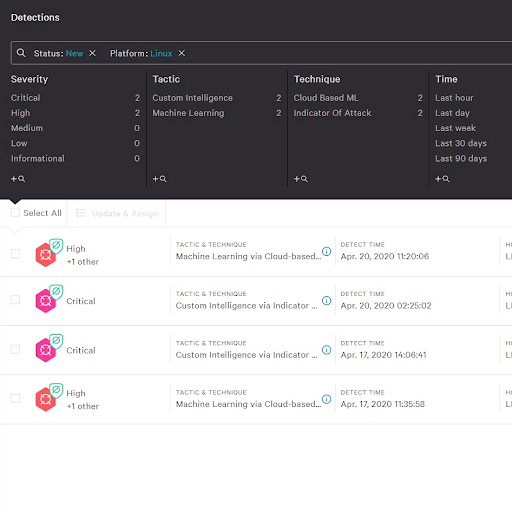
Falcon Cloud Security provides complete visibility into workload and container events and instance metadata enabling faster and more accurate detection, response, threat hunting and investigation, to ensure that nothing goes unseen in your cloud environment.
Falcon Cloud Security secures your entire cloud-native stack, on any cloud, across all workloads, containers and Kubernetes applications. Automate security and detect and stop suspicious activity, zero-day attacks, risky behavior to stay ahead of threats and reduce the attack surface.
Falcon Cloud Security supports Continuous Integration/Continuous Delivery (CI/CD) workflows allowing you to secure workloads at the speed of DevOps without sacrificing performance
“CrowdStrike allows tremendous visibility into all our endpoint assets, especially when they’re off our network. CrowdStrike also provides actionable alerts our team can manage and therefore they no longer have to waste resources chasing hundreds of false positives."
- Erik Hart, CISO, Cushman & Wakefield

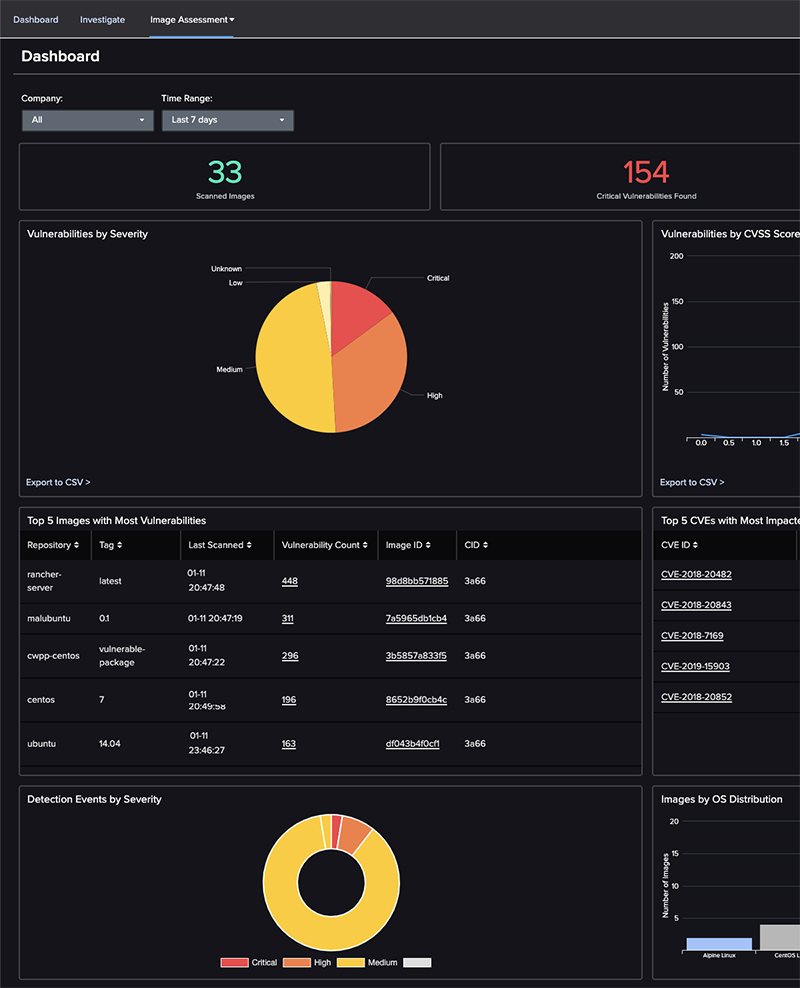
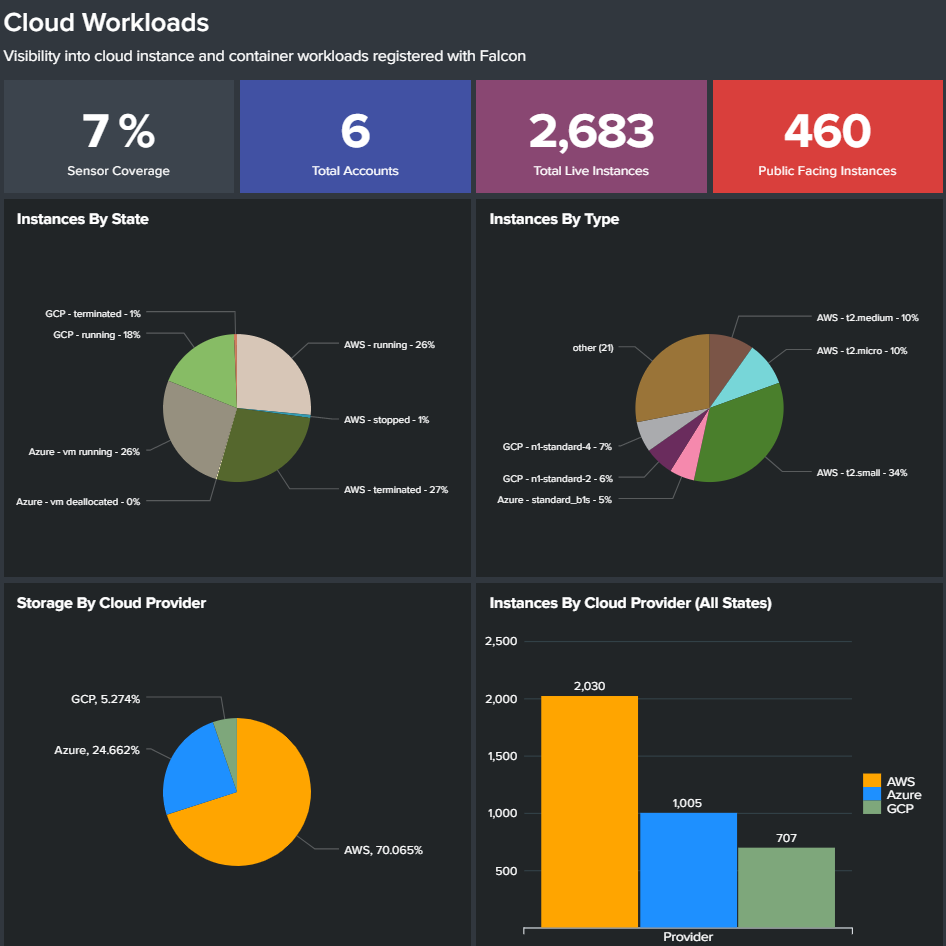
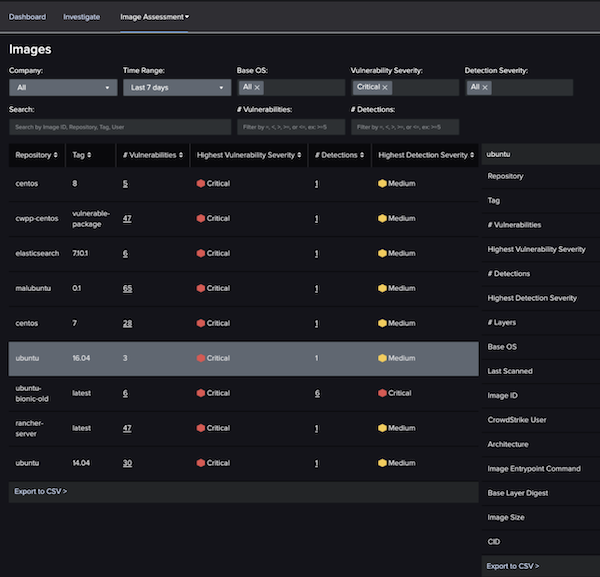
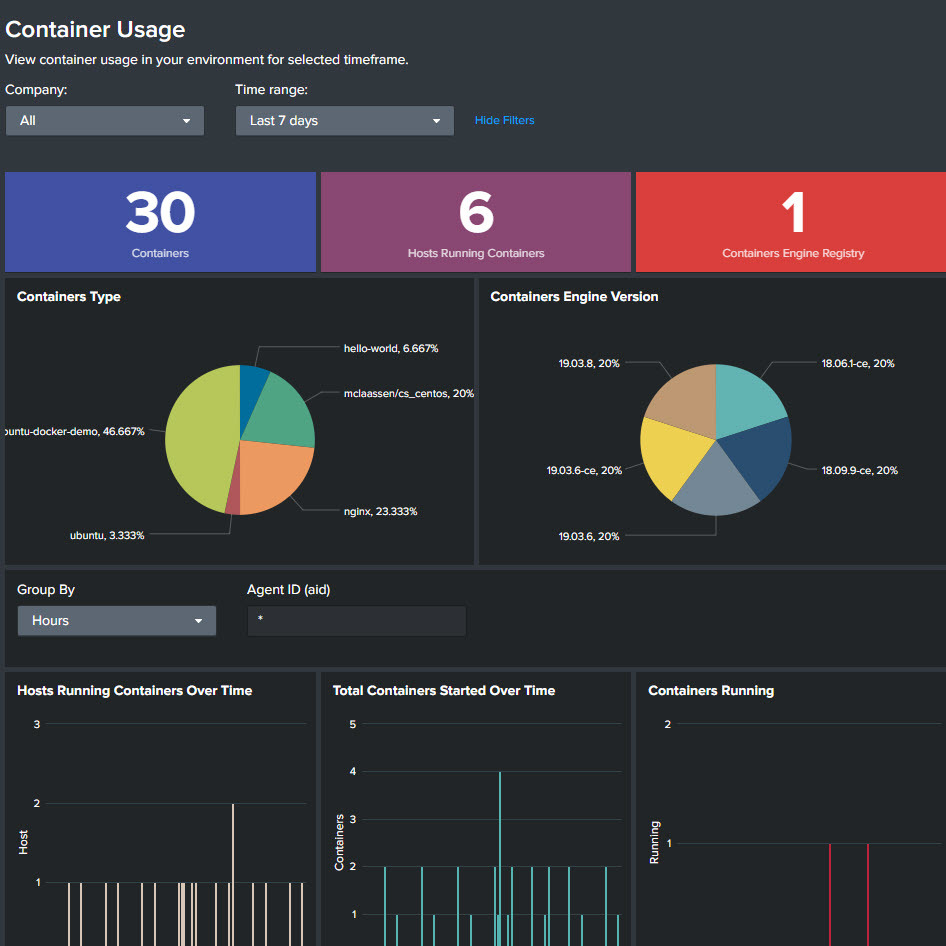


The first and only fully-managed CWP solution, delivering 24/7 expert security management, threat hunting, monitoring, and response for cloud workloads, backed by CrowdStrike’s industry-leading Breach Prevention Warranty.

Optimize your investments and get started faster
Click the links below to visit the CrowdStrike Integration Center

Click the links below to visit the CrowdStrike Integration Center

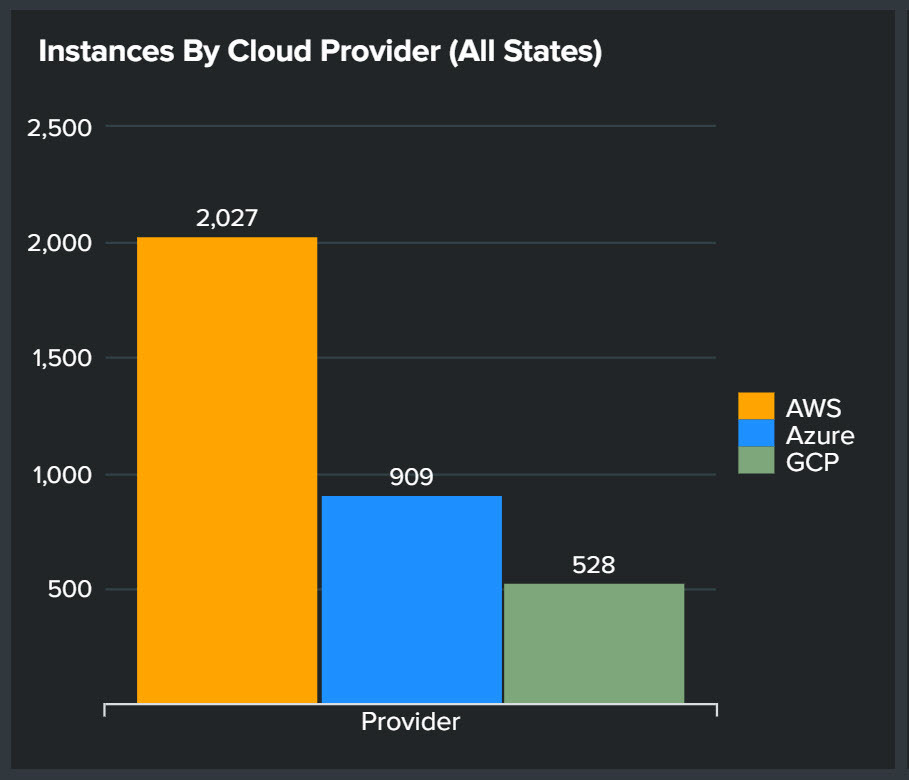
Provides multi-cloud visibility, continuous monitoring and threat detection, and ensures compliance enabling DevOps to deploy applications with greater speed and efficiency – cloud security posture management made simple.
The Falcon platform and intelligent, lightweight Falcon agent offer unparalleled protection and real-time visibility. Specifically tailored for containers, Falcon provides detailed insight into both the host and container-specific data and events.
Test and evaluate your cloud infrastructure to determine if the appropriate levels of security and governance have been implemented to counter inherent security challenges.






CrowdStrike is recognized by the top analysts, customers and partners as a global cybersecurity leader. Take a look at some of the latest Cloud Security recognitions and awards.

Learn more how CrowdStrike won the 2022 CRN Tech Innovator Award for Best Cloud Security.
Learn why Frost & Sullivan ranked CrowdStrike as a leader in Cloud-Native Application Security Platform (CNAPP).

Forrester has named CrowdStrike® Falcon Cloud Workload Protection as a Strong Performer in the Forrester Wave for Cloud Workload Security.
Report
2022 Frost Radar™ Leader: Crowdstrike’s Cloud-native Application Protection Platform (CNAPP)
Read More
Data sheet
Cloud Workload Protection Solution Brief
Download
White Paper
What You Need to Know When Selecting a Cloud Workload Protection Platform
Read More
Whitepaper
CrowdStrike 2022 Falcon Cloud Security, Cloud Workload Protection Buyers Guide
Read More
Report
Threat Landscape: Cloud Security
Read More
Blog
How CrowdStrike Increases Container Visibility
Read blog
Blog
To Get Cloud Security Cooking, You Need The Right Recipe For Success
Read blog
Blog
How CrowdStrike Protects Linux Hosts
Read blog