Falcon Cloud Workload Protection
CrowdStrike Falcon® Cloud Workload Protection provides comprehensive breach protection across private, public, hybrid and multi-cloud environments, allowing customers to rapidly adopt and secure technology across any workload.
Download Data Sheet
Benefits
Why Choose Falcon Cloud Workload Protection
-
![triage icon]()
Gain comprehensive visibility from a single console
Comprehensive visibility into workload events and instance metadata enables detection, response, proactive threat hunting and investigation, ensuring that nothing goes unseen in your cloud environments.
-
![Automatically discover cloud workload footprint]()
Automatically discover cloud workload footprint
Offers insight into the scope and nature of public, hybrid and multi-cloud cloud footprints so you can secure all workloads, uncover and mitigate risks, and reduce the attack surface.
-
![resources icon]()
Eliminate friction with key cloud integrations
Key integrations support continuous integration/continuous delivery (CI/CD) workflows allowing you to secure workloads at the speed of DevOps without sacrificing performance
Technical Features
What Sets Falcon Cloud Workload Protection Apart
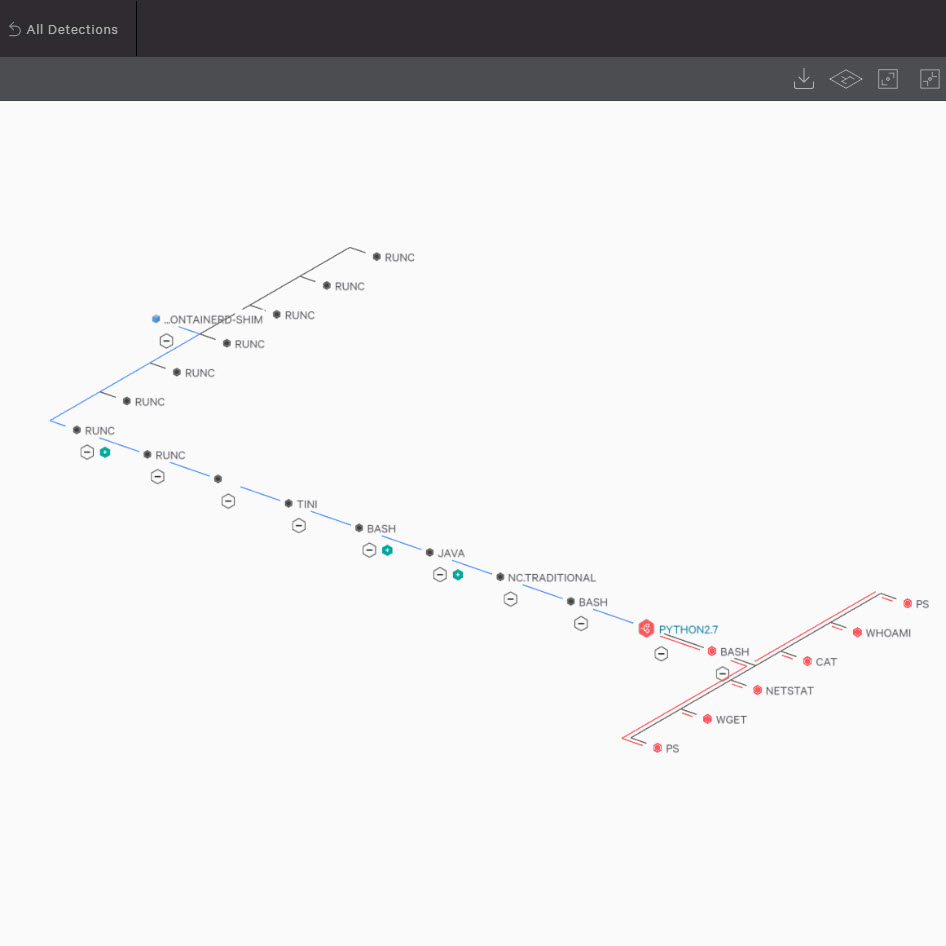
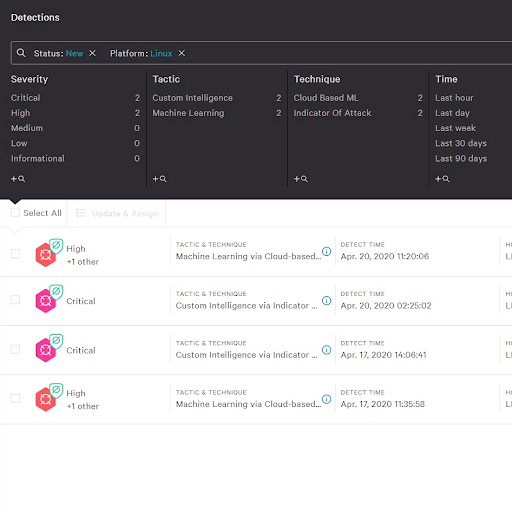
COMPREHENSIVE VISIBILITY INTO CLOUD WORKLOADS
- Gathers metadata at the instance level to easily identify owners of assets involved in an alert
- Continuous event monitoring provides visibility into workload activities, including activities running inside containers. A full set of enriched data and event details enables investigations against ephemeral and decommissioned workloads
- Offers proactive threat hunting across all workloads and endpoints from the same console
- Detects and investigates attacks that span multiple environments and different types of workloads, pivoting from endpoint to instances to containers
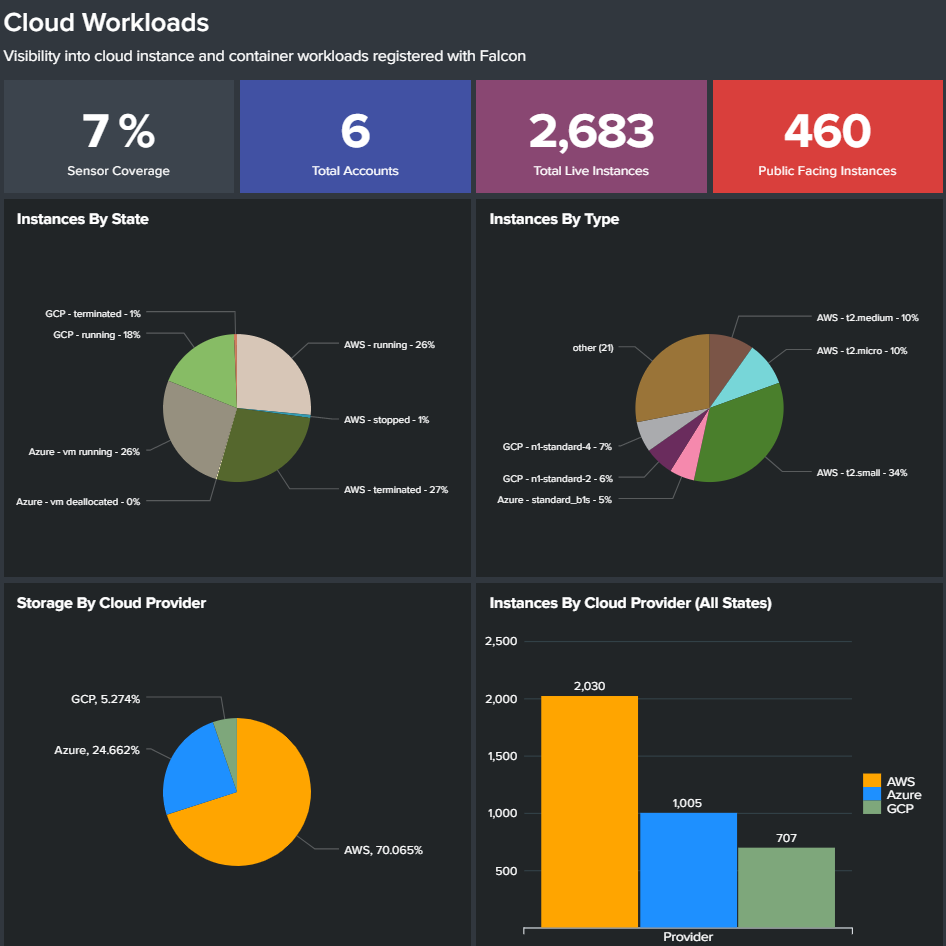
MULTI-CLOUD WORKLOAD DISCOVERY
- Provides insight into your cloud footprint so you can secure all workloads, uncover and mitigate risks, and reduce the attack surface
- Automatically discovers existing cloud workload deployments — without installing an agent — by enumerating AWS EC2 instances, GCP Compute instances, and Azure VMs
- Provides real-time information about workloads including context-rich metadata about system size and configuration, networking, and security group information for AWS, GCP, and Azure
- Identifies workloads that are not protected by the Falcon platform
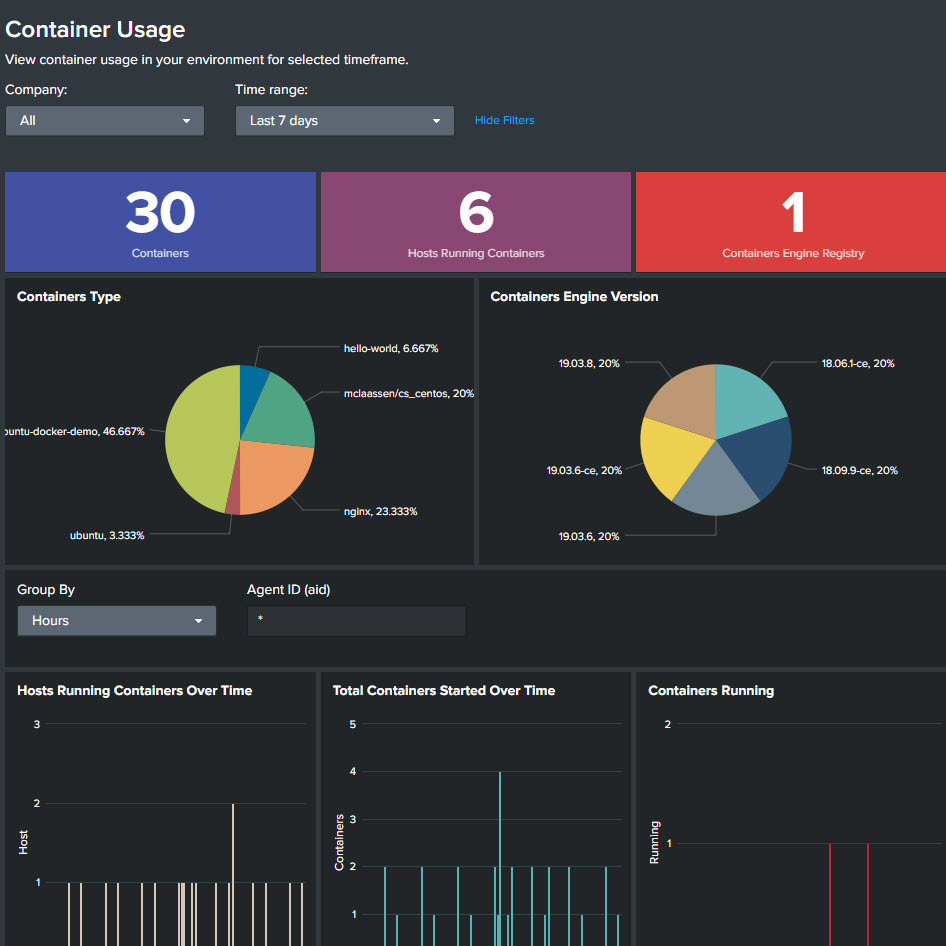
CONTAINER SECURITY
- Secures the host and container via a single Falcon agent running on the host, and runtime protection defends containers against active attacks
- Investigate container incidents easily when detections are associated with the specific container and not bundled with the host events
- Captures container start, stop, image, runtime information and all events generated inside the container, even if it only runs for a few seconds
- Visibility into container footprint includes on-premises and cloud deployments. Easily view container usage including trends and uptime, images used and configuration to identify risky and misconfigured containers
RUNTIME PROTECTION
- Combines the best and latest technologies to protect against active attacks and threats when workloads are the most vulnerable — at runtime
- Includes custom indicators of attack (IOAs), whitelisting and blacklisting to tailor detection and prevention
- Integrated threat intelligence blocks known malicious activities and delivers the complete context of an attack, including attribution
- Managed threat hunting 24/7 ensures stealthy attacks don’t go undetected
SIMPLICITY AND PERFORMANCE
Built in the cloud for the cloud, Falcon reduces the overhead, friction and complexity associated with protecting cloud workloads.
- One platform for all workloads — it works everywhere: private, public and hybrid cloud environments
- One console provides central visibility over cloud workloads regardless of their location
- Complete policy flexibility — apply at individual workload, group or higher level
- Scales as cloud workloads expand — no need for additional infrastructure
- Operates with only a tiny footprint on the host and has almost zero impact on runtime performance even when analyzing, searching and investigating
- Flexible consumption-based and annual-based subscription models support agile business planning

API-LED CLOUD INTEGRATIONS
Falcon eliminates friction to boost cloud security efficiency.
- Powerful APIs allow automation of CrowdStrike Falcon functionality, including detection, management, response and intelligence
- Chef, Puppet and AWS Terraform integrations support CI/CD workflows
- Google Cloud Operating System (OS) Configuration integration automates Falcon agent deployment directly from GCP, without the need for custom scripts
- AWS Private Link integration enables sensor-to-cloud traffic to flow via PrivateLink, reducing Internet exposure and simplifying network architectures


Product Validation



![[For Modules Only] 2019 GARTNER MAGIC QUADRANT (MQ) FOR ENDPOINT PROTECTION PLATFORMS (EPP)](https://cs-staging-www.crowdstrike.co.uk/wp-content/uploads/2019/10/Gartner_logo.png)
![[For Modules Only] THE FORRESTER WAVE: ENDPOINT SECURITY SUITES, Q3 2019](https://cs-staging-www.crowdstrike.co.uk/wp-content/uploads/2019/10/Forrester-Logo.png)